Why are organizations in the West subjected to relentless phishing and ransomware attacks? We need to go back in history for a bit to understand what caused this, and determine how we can best prepare ourselves.
First of all, let's look at planet Earth from the following perspective: It is an anarchy of nations. The United Nations has turned out to be a disappointing, ineffective, and corrupt mess. Credit where credit is due, the U.N. has done some very good work in certain corners. The Universal Declaration of Human Rights is a excellent example, but taken as a whole, the U.N. has mostly been paralyzed.
Now, let's go back to right after WWII. The cold war has started up, and there is a atomic arms race with mutually assured destruction as the only deterrent. Two superpowers at each other's throat with physical walls being built and the Iron Curtain coming down. I remember traveling with my parents passing CheckPoint Charlie from West- to East Berlin as boy, an unpleasant experience to say the least. Physical barriers were used to keep people both out and in, we have all seen the cold war spy movies, the images are vivid.
Fast forward 40 years.
The USSR fragments in 1991, and the Russian economy collapses. Communism implodes because that business model is not sustainable. At the time, there were roughly 800,000 official KGB agents in Russia. After the collapse, they spent ten years morphing into the FSB, all the while expanding and absorbing other instruments of power, including criminal networks, other security services, economic interests, and parts of the political elite.
The West loses it's arch enemy, starts enjoying peace and focuses less on NATO as their main defensive force against the USSR. The strong anti-USSR values that bind the West together no longer hold and the world order that America depends upon starts to come apart.
During those 40 years, the cold war has gone underground, it transforms to some degree in covert actions committed by both the CIA and the FSB, and overt actions like propaganda campaigns by both sides which are very much going on today.
Former Soviet satellite states are disillusioned with the NATO and the west, and at the moment believe they have to fend for themselves -- or even having to defend their sovereign territory against Russian aggression like the Ukraine.
In Moscow, Vladimir Putin is playing the long game
In Moscow, Vladimir Putin is playing the long game and is leveraging this unraveling of the Western world order as fast as he can. He is trying to make Russia into a superpower again, and uses everything he can in his spook toolkit including the asymmetrical hybrid information warfare we see today.
The last two administrations have failed to see that the West is already at war, whether it wants to be or not. I am quoting Molyy McKew here, who has been an advisor to Eastern European governments: "It may not be a war we recognize, but it is a war. This war seeks, at home and abroad, to erode our values, our democracy, and our institutional strength; to dilute our ability to sort fact from fiction, or moral right from wrong; and to convince us to make decisions against our own best interests." Interesting that this last is one of the definitions of social engineering.
The current war is one of subversion more than domination. These shadow tactics are what the KGB starred in and what Vladimir Putin learned when he came up through the KGB ranks.
A large majority of Russians who were shocked by the economic and social hardships of the 1990s applauded Putin as the strongman who built a new security state, even though his Kleptocracy weakened the Russian economy and civic institutions. Looking at Russia today, it's a gas station with a flag on it, with an overblown police force and a criminal economy the size of Italy. Oh, and the world’s largest nuclear arsenal...
Putin is operating on a very old, very successful principle that to keep your own group together, there is nothing better than having a mutual enemy. Putin wants the West to fragment and become as weak and broken as they perceive themselves to be.
Putin’s Russia needs the USA to be its enemy Number One
In short, Putin’s Russia needs the USA to be its enemy Number One. It's a war that needs to be won and its goal is an unstable new world of "all against all" where Putin can be a strong player. Keep in mind that it's a combined war machine, Russia's hard power and the technological, information, economic, cultural and criminal tools are all used toward this strategic objective. Here is where Gen. Valery Gerasimov's doctrine comes in. He's the chief of Russia’s General Staff. In his 2013 article, Gerasimov talked about the Russian military’s desire to hone its hacking skills as an extension of conventional warfare and political conflict.
It is also where the criminal hackers fit right in that harrass Western corporations and non-profits. They are all part and parcel of Putin's much larger campaign of destabilization. They are not going away any time soon.
There is one parallel between global geopolitics and IT security. Used to be in the early days with dumb terminals and no mobile devices that firewalls actually worked, similar to the Iron Curtain. But now with the traditional periphery gone and BYOD all over the place, firewalls are not that effective and the end-user really needs to be your human firewall.
That end-user needs to be trained to recognize social engineering attacks and efforts to manipulate them by highly sophisticated Eastern European bad actors.
There is something that can be done about this...
The vast majority of these attacks start with phishing. KnowBe4's integrated training and phishing platform allows you to send fully simulated phishing emails so you can see which users answer the emails and/or click on links in them or open infected attachments. If you have a Platinum subscription you can even send them "vishing" attacks straight to the phone on their desk.
See it for yourself and get a live, one-on-one demo.
Request A Demo
https://info.knowbe4.com/kmsat-request-a-demo
Warm regards,
Stu Sjouwerman
CEO, KnowBe4, Inc.

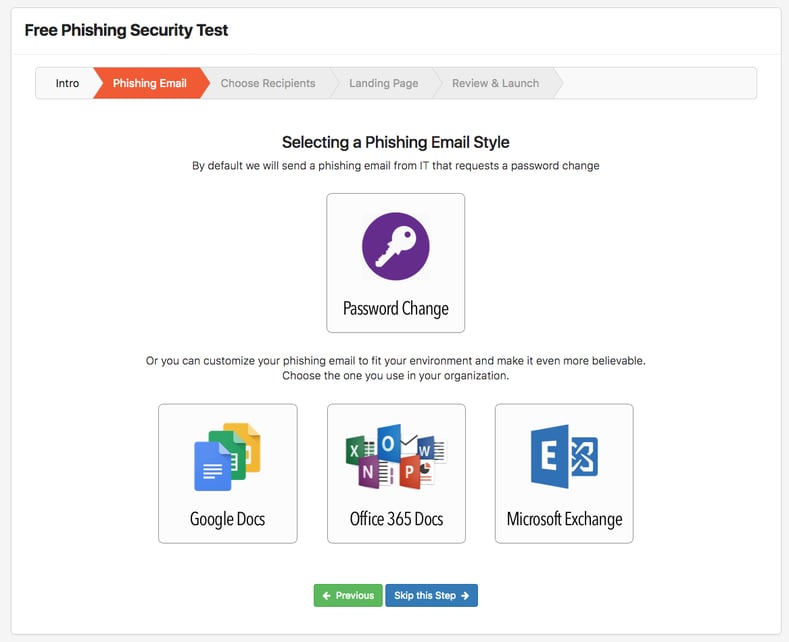

 with our free Phishing Security Test (PST). If you don't do it yourself, the bad guys will.
with our free Phishing Security Test (PST). If you don't do it yourself, the bad guys will.






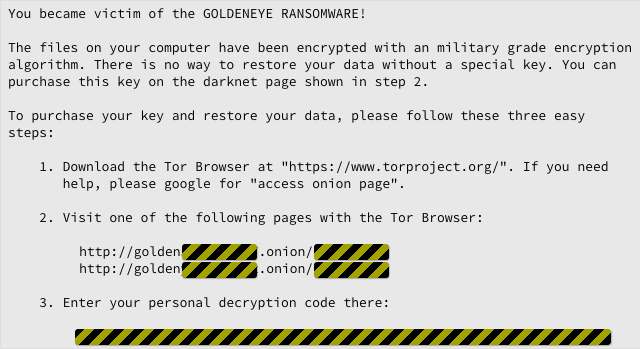
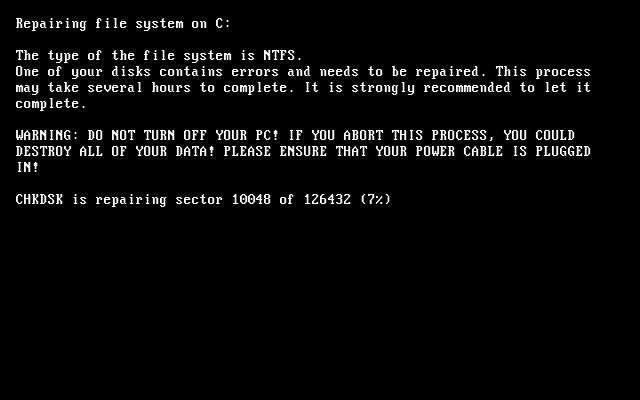

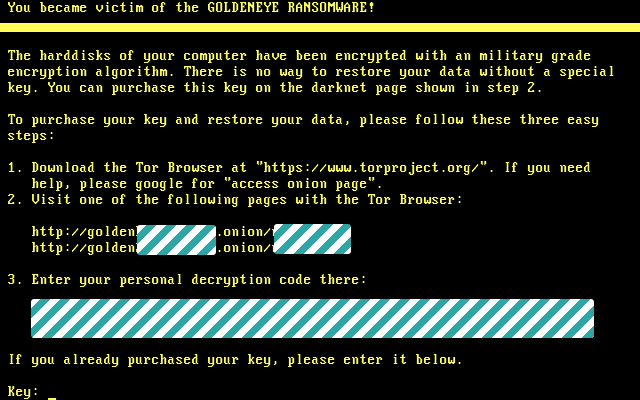
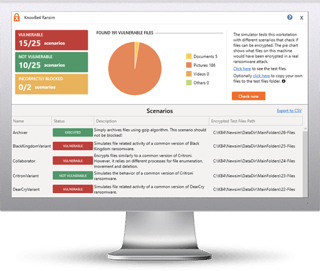



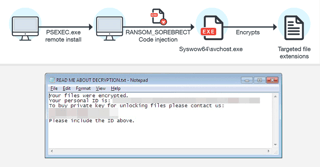 Security researchers have discovered a new fileless ransomware in the wild, which injects malicious code into a legitimate system process (svchost.exe) on a targeted system and then self-destructs itself in order to evade detection by antivirus.
Security researchers have discovered a new fileless ransomware in the wild, which injects malicious code into a legitimate system process (svchost.exe) on a targeted system and then self-destructs itself in order to evade detection by antivirus.