CEO Fraud Attacks Were Far More Lucrative than Ransomware over the Past 3 Years
-
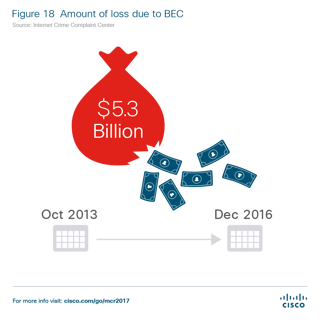
Cisco's midyear report released this week showed that CEO Fraud netted cybercrime five times more money than ransomware over the last three years.
The surprising highlight of Cisco's ninety page report was that cybercrime made $5.3 billion from CEO Fraud attacks --called business email compromise (BEC) by the FBI-- compared with a "mere" $1 billion for ransomware over a three-year stretch,
Organized Eastern European cybercrime is more and more taking the "time is money" approach, in this case billions, says Steve Martino, Cisco's chief information security officer. "What we are looking at is the continual commercialization of cyberattacks," Martino says, pointing out that is a major theme in the report.
Malicious ransomware takes time to develop and extensively test before any net Bitcoin comes into the wallet, compared to doing a quick bit of research on LinkedIn and crafting a spoofed spear phishing attack. CEO Fraud simply is faster to pull off. Moreover, your run-of-the-mill spray-and-pray ransomware attacks are often lower-dollar numbers.
Schooling Users on CEO Fraud and Ransomware
Cisco's Martino says targeted cybersecurity education for employees can help prevent users from falling for CEO Fraud and ransomware attacks. The finance department could especially benefit from security training on phishing campaigns, so when the bogus email comes across the transit of the CEO asking for a funds transfer it can be detected, Martino says.
Regular software patching also is crucial. When spam laden malware hits or ransomware attacks similar to WannaCry surfaces, the impact can be minimized. "People focus on new technology, but forget about patching and maintaining the infrastructure," Martino observed.
And a balanced defensive and offensive posture, with not just firewalls and antivirus but also including measures to hunt down possible attacks through data collection and analysis, he adds.
Spyware Makes A Comeback
Cisco found that in the first half of this year, attackers altered their methods of delivering, hiding, and evading their malicious packages and techniques.
Fileless malware is popping up, which lives in memory and deletes itself once a device restarts, according to the report. As a result, it makes detection and the ability to investigate it more difficult.
Additionally, attackers are also making use of anonymized and decentralized infrastructures, such as Tor proxy services, to hid command and control activities.
Meanwhile, three families of spyware ran rampant, with Hola, RelevantKnowledge, and DNSChanger/DNS Unlocker affecting more than 20% of the 300 companies in the sample for the report.
Ironically, however, many companies and organizations underestimate or virtually dismiss spyware. "Spyware is being disguised as adware and adware, unlike spyware, does not create damages for a company," says Franc Artes, Cisco's Security Business Group architect. He adds that attackers are injecting spyware and other forms of malware into adware, since adware is a low priority for security teams.
Download Your CEO Fraud Prevention Manual
CEO fraud has ruined the careers of many executives and loyal employees. Don’t be next victim. This brand-new manual provides a thorough overview of how executives are compromised, how to prevent such an attack and what to do if you become a victim.
Download The Manual Here:
https://info.knowbe4.com/ceo-fraud-prevention-manual
Warm regards,
Stu -
I'm really not so surprised about this. It's really difficult to prevent targeted fishing attacks, no matter how well educated users are.
-
People always remains the weak link.
-
Sales people at my old company were always clicking on links and entering their info. 2FA seems like the only way to stop it.
-
@bigbear said in CEO Fraud Attacks Were Far More Lucrative than Ransomware over the Past 3 Years:
Sales people at my old company were always clicking on links and entering their info. 2FA seems like the only way to stop it.
Really? How does that stop them?
-
You get an email, it says "hey some guy you know is sharing a google doc or whatever, you need to sign in"
Then you pick on the website whethere you use Office 365, Google Apps, etc
Next thing you know the doc says cannot be found, so you forget about it. Meanwhile all your information has been compromised and it starts sending out emails to your contacts list.
With 2FA there is no way to use your login information because the attacker cant get that second stage of info when logging in. From what I have seen those phishing attempts dont even attempt to collect it.
Of course, thats hardly the only type of socially engineered attack.
-
@bigbear said in CEO Fraud Attacks Were Far More Lucrative than Ransomware over the Past 3 Years:
You get an email, it says "hey some guy you know is sharing a google doc or whatever, you need to sign in"
Then you pick on the website whethere you use Office 365, Google Apps, etc
Next thing you know the doc says cannot be found, so you forget about it. Meanwhile all your information has been compromised and it starts sending out emails to your contacts list.
With 2FA there is no way to use your login information because the attacker cant get that second stage of info when logging in. From what I have seen those phishing attempts dont even attempt to collect it.
Of course, thats hardly the only type of socially engineered attack.
Good attacks definitely do get and pass that info through.