[ALERT] Looks Like A New Worldwide Ransomware Outbreak
-
Motherboard reported: "A quickly-spreading, world-wide ransomware outbreak has reportedly hit targets in Spain, France, Ukraine, Russia, and other countries.On Tuesday, a wide range of private businesses reportedly suffered ransomware attacks. Although it is not clear if every case is connected, at least several of them appear to be related to the same strain of malware."
Motherboard continued: "The attacks are similar to the recent WannaCry outbreak, and motherboard has seen several reports of infections shared by victims on Twitter. We were not able to immediately confirm the veracity of the reports, but several security researchers and firms also reported the attacks.
"We are seeing several thousands of infection attempts at the moment, comparable in size to Wannacry's first hours," Costin Raiu, a security researcher at Kaspersky Lab, told Motherboard in an online chat.
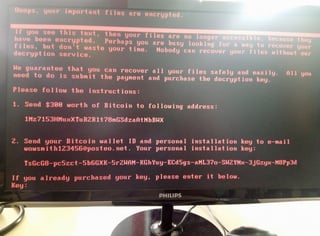
Judging by photos posted to Twitter and images provided by sources, many of the alleged attacks involved a piece of ransomware that displays red text on a black background, and demands $300 worth of bitcoin.
"If you see this text, then your files are no longer accessible, because they are encrypted," the text reads, according to one of the photos. "Perhaps you are busy looking for a way to recover your files, but don't waste your time. Nobody can recover your files without our decryption service."
Raiu believes the ransomware strain is known as Petya or Petrwrap, a well-known type of ransomware. According to a tweet from anti-virus company Avira, the Petya attacks were taking advantage of the EternalBlue exploit previously leaked by the group known as The Shadow Brokers (Motherboard could not independently confirm this at the time of writing).
EternalBlue is the same exploit used in the WannaCry attacks; it takes advantage of a vulnerability in the SMB data-transfer protocol, and Microsoft has since patched the issue. However, whether customers apply that patch is another matter.
Security researchers from Kaspersky Lab reported that the ransomware hit Russia, Ukraine, Spain, France, among others. Several people on Twitter reported witnessing or hearing reports of the outbreak in their respective countries, and across a wide range of industries. Companies around the world also reported computer outages.
If You Have Not Done So Yet, Apply This Patch Immediately.
From what we have been able to learn, this new worm spreads through SMB jkust like WannaCry so when we're talking about machines behind firewalls being impacted, it implies ports 139 and 445 being open and at-risk hosts listening to inbound connections. It'd only take one machine behind the firewall to become infected to then put all other workstations and servers at risk due to it being a true worm.
In the meantime, harden yourselves against this Windows Network Share vulnerability and ensure that all systems are fully patched with the "MS17-010" security update (link below) and remind all staff to Think Before They Click when they receive any out of the ordinary emails. https://technet.microsoft.com/en-us/library/security/ms17-010.aspx
Note, the patch is included in the Monthly Quality rollups.
-